Introduction: Why Hardware Security Matters
When people think about Android security, they usually picture passwords, biometrics, or encryption. But in the world of custom Android device development, security starts much deeper—at the hardware level. One of the most important but least understood tools in this space is the eFuse.
For companies designing and manufacturing their own Android hardware, eFuse technology plays a vital role in keeping devices secure, protecting intellectual property, and ensuring firmware integrity. It has become a key part of the production process for brands ranging from consumer smartphones to industrial IoT devices. In this article, we’ll dive into what eFuse is, how it works, who uses it, its advantages, drawbacks, and best practices for any team working on a custom Android device.
What is eFuse?
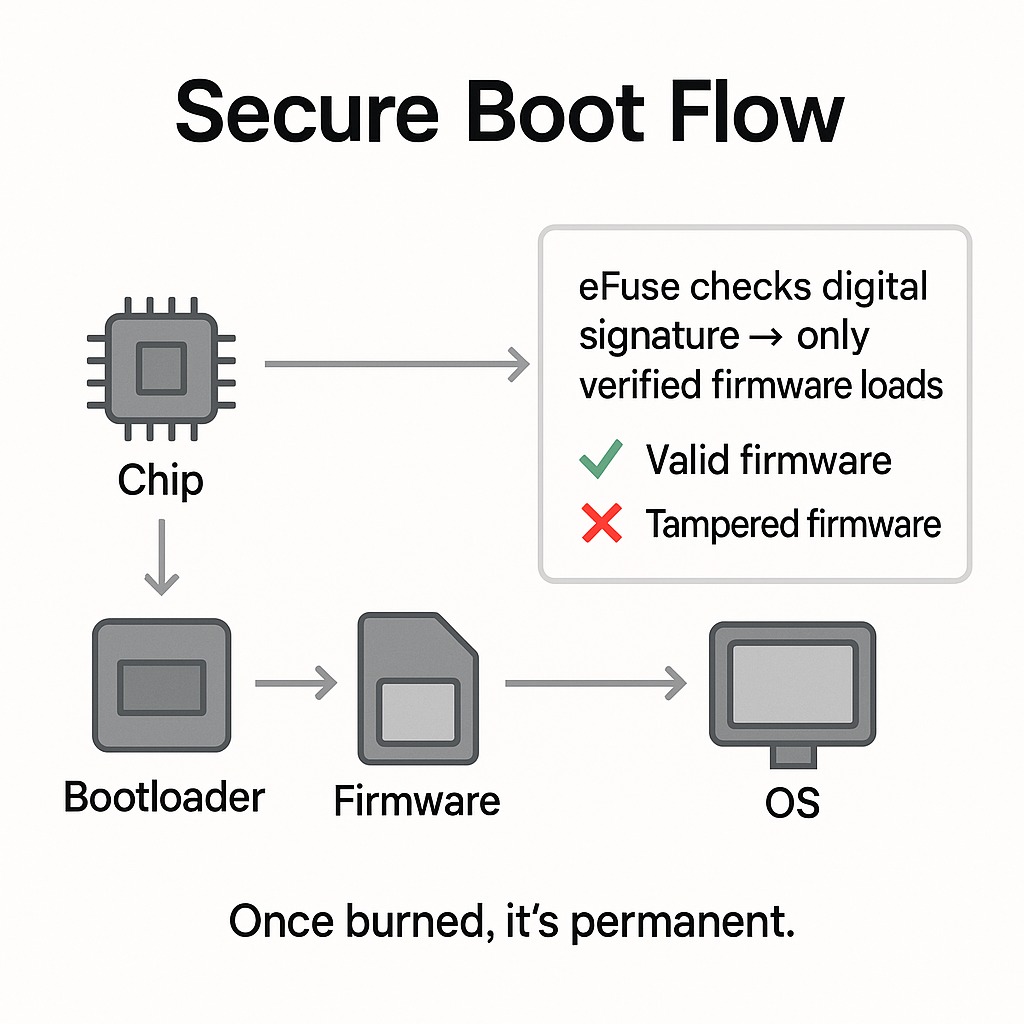
At its simplest, an eFuse (short for “electronic fuse”) is a tiny piece of programmable memory built directly into a system-on-chip (SoC). Unlike traditional storage, eFuse bits are one-time programmable (OTP)—once you “blow” a fuse, it permanently changes state and cannot be reversed.
Think of eFuse like a light switch that can only ever be flipped once. Once it’s set, there’s no turning it back. This permanent change makes eFuse especially useful for storing critical, security-related information such as:
- Cryptographic keys for secure boot
- Device identity information
- Version numbers to prevent rollback attacks
- Warranty and repair indicators
In the context of custom Android hardware manufacturing, eFuse provides a way to “lock in” important security decisions at the factory level, ensuring every device that ships is consistent and protected.
How Does eFuse Work?
Technically, eFuse works by physically altering tiny conductive links inside the chip. When a manufacturer programs an eFuse, a small electrical charge permanently blows that link, changing its binary value from 0 to 1 (or vice versa). Unlike flash memory, this change cannot be undone, rewritten, or erased.
From a software perspective, the system’s bootloader or operating system can query the state of these fuses during startup. For example:
- If the secure boot eFuse is set, the bootloader will only load signed and verified firmware.
- If an anti-rollback fuse indicates that version 3 is the minimum acceptable firmware, the device will refuse to boot version 2, even if someone tries to flash it.
This is how smartphone manufacturers prevent users—or attackers—from downgrading firmware to versions with known vulnerabilities. For custom Android device developers, this mechanism ensures that once the device is in the field, its software integrity can’t be easily bypassed.
Who Uses eFuse?
Nearly every major semiconductor and mobile manufacturer makes use of eFuse technology. Here are some of the most well-known examples:
- Qualcomm: Uses eFuses for secure boot, device attestation, and digital rights management.
- MediaTek: Integrates eFuses in its chipsets for bootloader security and rollback protection.
- Samsung: Implements the famous “Knox Warranty Bit,” an eFuse that flips if a device is rooted or flashed with unofficial firmware.
- NXP / STMicroelectronics: Apply eFuses in industrial and automotive contexts where tamper resistance is critical.
- Apple (though not Android): Uses a similar concept for unique device identifiers and firmware locks.
For teams building a custom Android device, it’s helpful to know that the same eFuse mechanisms found in flagship smartphones are also available in the chipsets you might use for smaller-scale or specialized hardware projects.
Why is eFuse Useful in Custom Android Devices?
In today’s connected world, the stakes for device security are high. A vulnerability in your hardware can lead to data breaches, IP theft, or compromised user trust. eFuse is a powerful line of defense for several reasons:
- Secure Boot Enforcement
With eFuse, you can lock a custom Android device so it only boots firmware signed by your team. This stops unauthorized software from running, protecting both your brand and your users. - Rollback Protection
By burning version numbers into eFuse, you can prevent attackers from downgrading a device to older, vulnerable firmware. - Unique Device Identity
eFuse can store cryptographic keys that make each device unique. This is essential for enterprise authentication, payment systems, or secure IoT applications. - Intellectual Property Protection
For OEMs, eFuse can help prevent cloning and counterfeit devices by ensuring only your signed software will run on your hardware. - Compliance with Security Standards
Many enterprise and government contracts require hardware-backed security features. eFuse helps custom Android hardware manufacturers meet these expectations.
Different Use Cases for eFuse
eFuse isn’t limited to smartphones. It plays a role in many categories of devices:
- Consumer Electronics: Locking bootloaders in smartphones, tablets, and smart TVs.
- Enterprise Devices: Ensuring company-owned devices can’t be rooted or modified.
- Payment Terminals: Preventing tampering or unauthorized software installations.
- Industrial IoT: Protecting edge devices that control critical infrastructure.
- Network Equipment: Enforcing trusted firmware in routers, gateways, and custom Android-based modems.
For companies creating a custom Android device, the flexibility of eFuse means you can tailor its use to your industry—whether you’re building for consumers, enterprises, or specialized markets.
When eFuse May Not Be a Good Option
Despite its strengths, eFuse isn’t always the right choice. Its permanent nature introduces some challenges:
- Irreversible Changes
Once an eFuse bit is set, it’s set forever. If you make a mistake in programming, there’s no undo button. This can be risky during prototyping or early production runs. - Bricking Risks
If a secure boot fuse is burned incorrectly, you can accidentally make a device unbootable. - Overkill for Low-Security Devices
Not every product needs the highest level of hardware security. For inexpensive consumer gadgets or short lifecycle products, eFuse might add unnecessary complexity. - Limited Flexibility
eFuse is not updatable. In contrast, software-based solutions (like trusted execution environments or secure elements) can sometimes be updated in the field.
Does eFuse Damage the CPU or Memory?
A common misconception about eFuse is that it “destroys” a chip if unauthorized firmware is loaded. In reality, that’s not how eFuse works.
eFuse does not burn out the CPU or physically damage memory. Instead, it serves as a security checkpoint. When firmware doesn’t match what the eFuse values expect, the system simply refuses to boot. To the user, this might look like the device is “bricked,” but it’s actually a protective lockout — not hardware destruction.
For example:
- In a custom Android device, if secure boot fuses are set, the bootloader will only accept signed firmware. Any tampered or downgraded version will be blocked at startup.
- In Samsung devices, the Knox eFuse flips if unofficial firmware is installed, permanently disabling some features — but the hardware remains intact.
True “self-destruct” mechanisms do exist in certain military or defense chips, but consumer-grade SoCs from Qualcomm, MediaTek, or NXP don’t use eFuse this way. For most device makers, the worst-case scenario is a device that won’t boot unauthorized code, not one that fries its CPU.
Best Practices for Using eFuse in Custom Android Hardware
If you decide to leverage eFuse in your product, here are some practical guidelines:
- Program eFuses at the End of Manufacturing
Don’t burn critical fuses during prototyping. Wait until final testing and quality assurance. - Double-Check Your Keys and Versions
Build strict workflows to verify signatures, hashes, and version numbers before programming. - Pair eFuse with Other Security Features
Combine with TPMs, secure elements, or software-based integrity checks for layered security. - Work Closely with Chipset Vendors
Documentation from companies like MediaTek and Qualcomm can be complex. Rely on their resources to avoid costly mistakes.
For OEMs and startups alike, eFuse is best handled with a cautious, structured process—especially when building custom Android devices at scale.
Closing Thoughts
eFuse is one of those hidden technologies that quietly powers the security of many modern smartphones, IoT devices, and custom Android devices on the market. It provides a permanent, tamper-resistant anchor for security decisions, ensuring that only trusted software can run on your hardware.
But with that power comes responsibility. Once you burn an eFuse, there’s no going back. For device makers, this means balancing the benefits of bulletproof security with the risks of irreversibility.
At Hatch, we help companies navigate these trade-offs in custom Android hardware manufacturing. Whether you’re designing for consumers, enterprises, or industrial markets, understanding eFuse is key to building secure, reliable, and trusted devices.


